WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
There are a keyword that is popular in our cyber community, Man-in-the-Middle. A man in the middle of what? What is this term?
It turns out that Man-in-the-Middle is a cyber attack that is conducted when the packet is still in the transport process, or still in the air.
The key principle of it is interception. How does it work?
In the normal connection, the packet will be, sent straightforward to the destination.

However, if the Man-in-the-Middle occurred, the things will become as below:

The packets that supposed to be sent straight to the destination are being intercepted by the third party. It will cause a serious threats for credentials, or even worse, unwanted transactions.
That is the simple explanation of Man-in-the-Middle.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
In one of my posts, I had demonstrated you how to use reverse TCP by pentestmonkey. But, how does reverse tcp works? In this post, we’re going to take a closer look at reverse TCP.
If the client requesting something to the server, that is forward TCP connection. Basically, the server will send a regular response as usual.
When doing something illicit, e.g. request poisoning, to the server, if the server implement proper security to handle it, the attack will be failed.
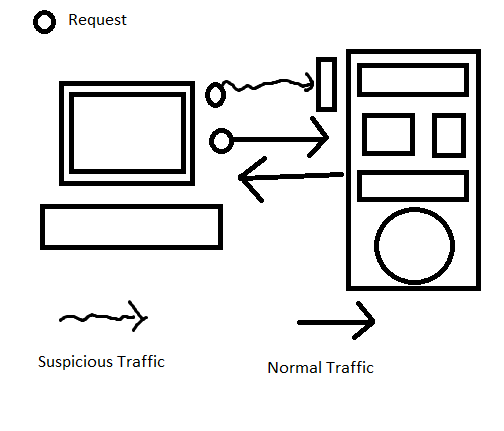
But, what happen if the, position of both is inverted? That is the thing that will cause serious security Issue.
In reverse TCP, server is the one that sent the request, and the client is the one that is responded to the request.
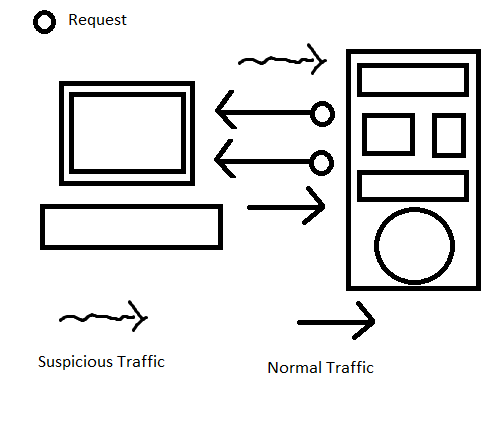
This kind of connection is dangerous, due to the firewall doesn’t block the illicit response, unlike when if the packet is a request.
That is why there are a significant number of Reverse TCP attacks.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
DirBuster is a tool by OWASP to brute-forcing directories. It is good enough because it can find directories and files that are usually hidden in the website.
However, DirBuster only available as GUI application and it is hard to use when it comes to brute-forcing using large word-lists. So, what’s the alternative?
Well, there is a tool named dirsearch. The tool is available here:
https://github.com/maurosoria/dirsearch
To use that, it is simple. Just type:
python dirsearch.py -u target_url
The result will be like this:
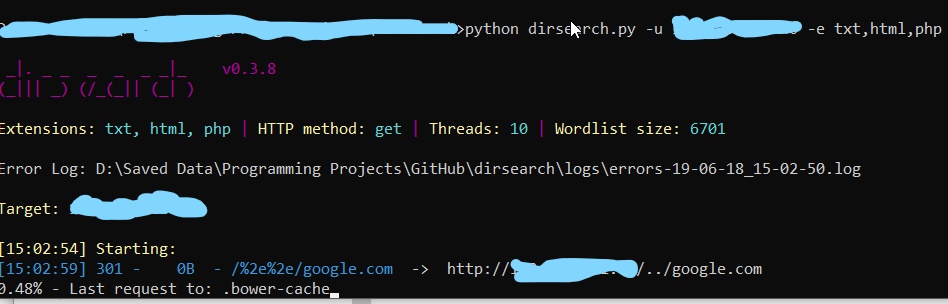
Later, it can be customize to do recursion:
-r –> Enable Recursion
–R value —>Maximum Recursion sub-folders level
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
Burp Suite is one of the many tools tat is used to intercept and modify HTTP Request. It is a powerful tool to modify http request during loading process.
In this post , I’m going to explain how to set up Burp Suite.
First, open the Burp Suite. It will show something like this:
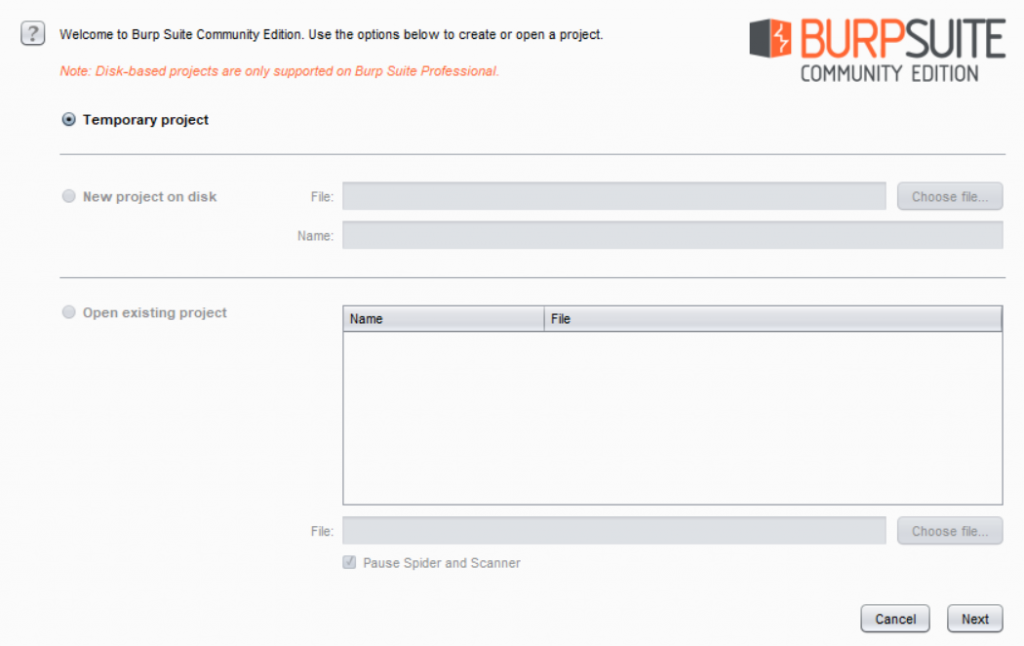
Select “Temporary project”, then next. It will show again something like this:
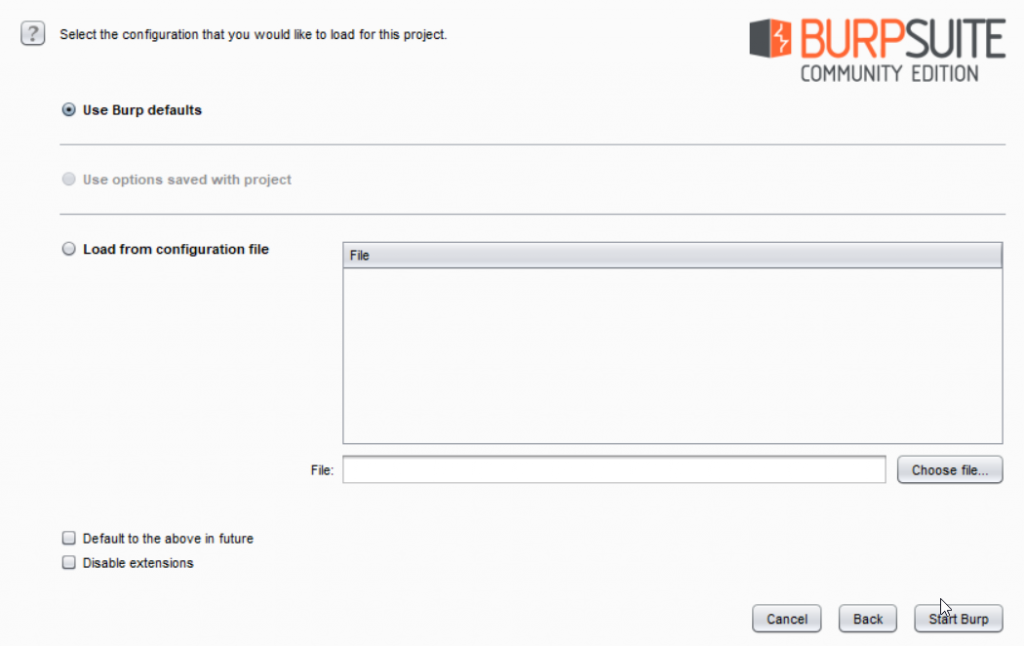
Select “Use Burp default”, then click “Start Burp”. The Picture below is the main interface of Burp Suite:
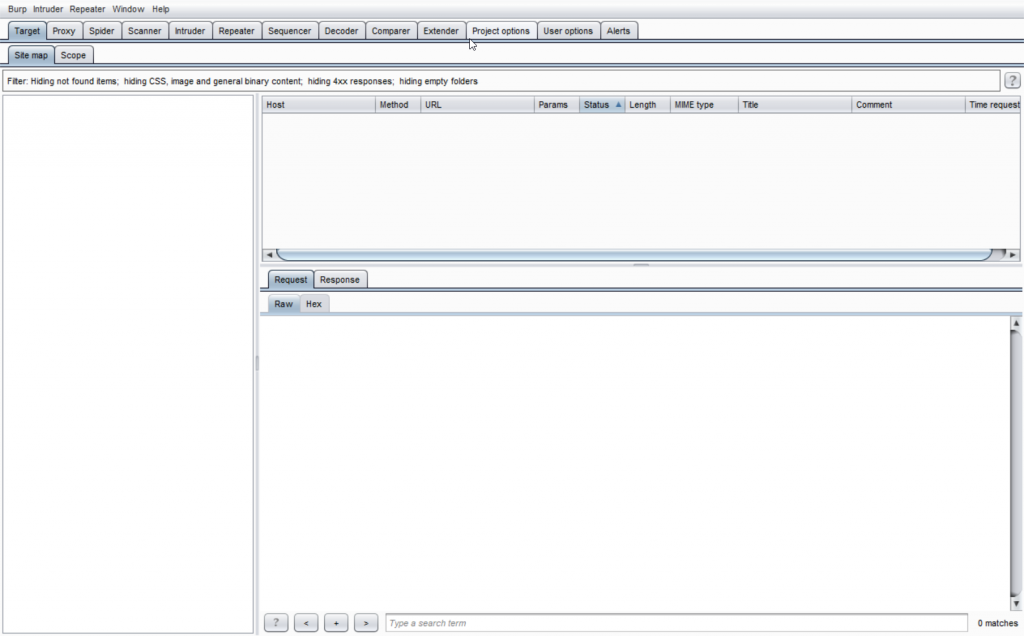
Open Proxy>Options
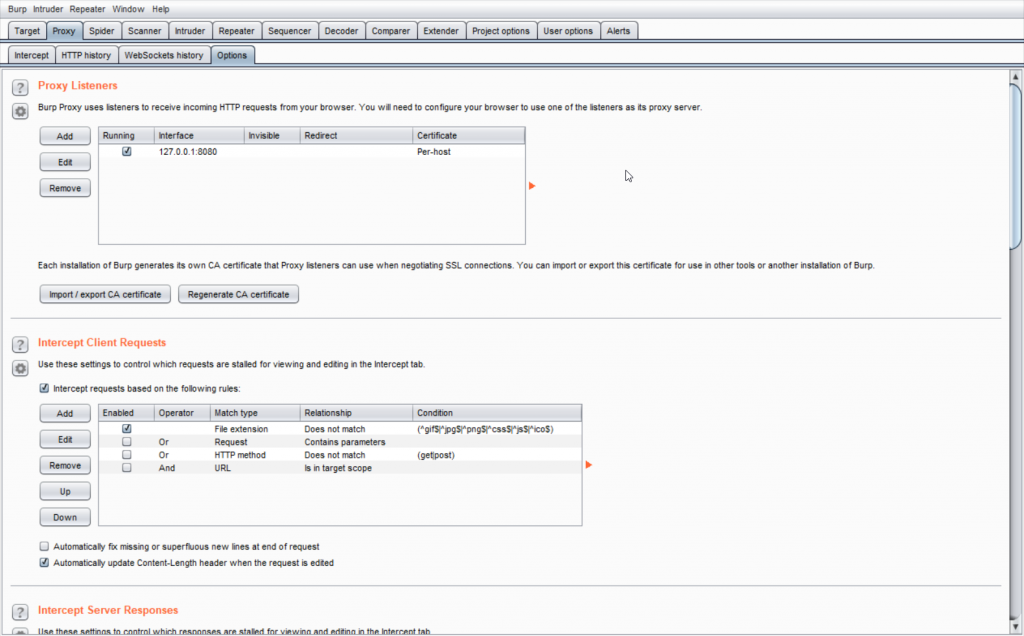
Check whether Proxy listener is correct or not. Then configure your browser proxy to use IP 127.0.0.1.
Here is the link how to configure it:
Chrome: https://support.portswigger.net/customer/portal/articles/1783065-Installing_Configuring%20your%20Browser%20-%20Chrome.html
Firefox: https://support.portswigger.net/customer/portal/articles/1783066-Installing_Configuring%20your%20Browser%20-%20FF.html
Then, open Proxy>Intercept and turn on the Intercept.
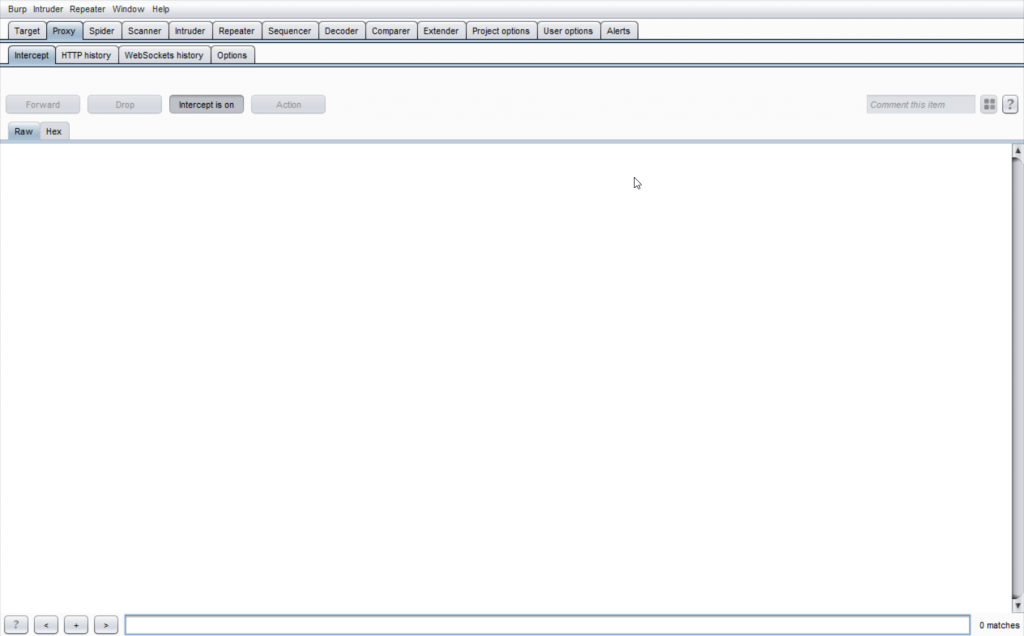
Open Browser, type: http://burp
Then, download the certificate.
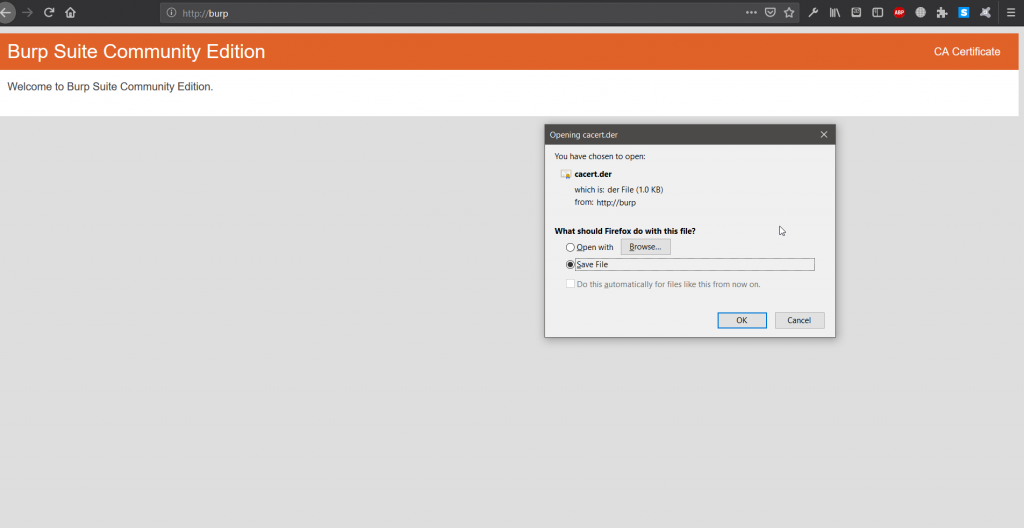
Install the certificate to your browser, and you ready to go.
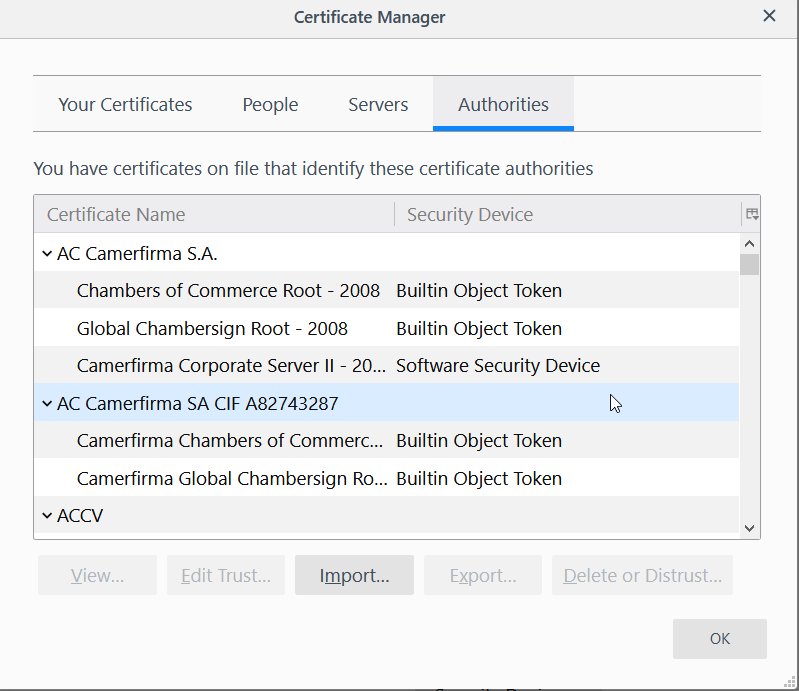
Then you can now use Burp Suite. That’t it. Burp Suite is ready to Intercept. That’s how you set up Burp Suite proxy.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
Previously, were talking about how to find real IP. In this post, we’re going to find out how prove that the IP is the real server IP.
First step is test the IP by type it into web browser.
![]()
If it show same page as your target, move into second phase, WHOIS.
type the following command:
<pre>
111.111.111.111
</pre>
If it shows the name of one of the CDN providers, that is NOT your target. Else, it is your target.
Sometimes, the target refused the connection to their real IP addresses. It only allow the connection using URL.
That is how you identify whether it is real IP or not.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
Last time, We’re talking about Censys.io, a tool to find real IP addresses. This time, we’re going to talk about the alternative of it.
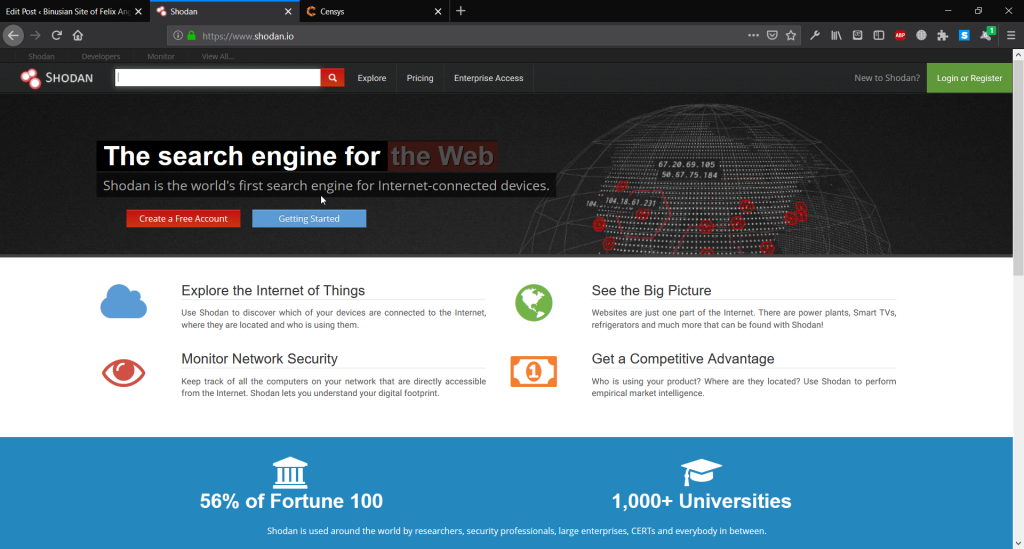
This is Shodan.io, another tool to find a real IP addresses. If we take a look closer, the position of search box is at the top of the page. It can be very inconvenient for some people.
However, when you search for the real server IP, it will show something like this:
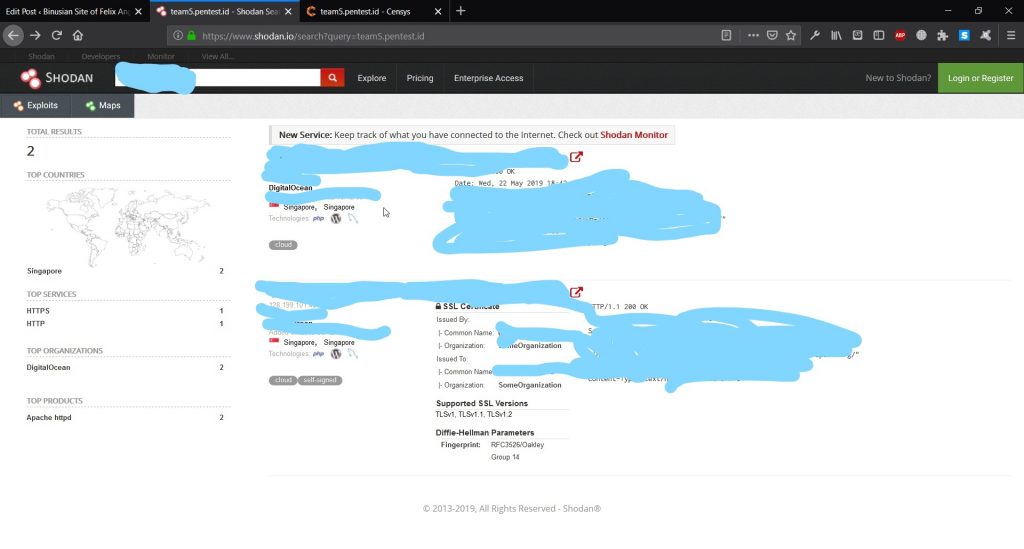
It woll only show necessary thing that you need.
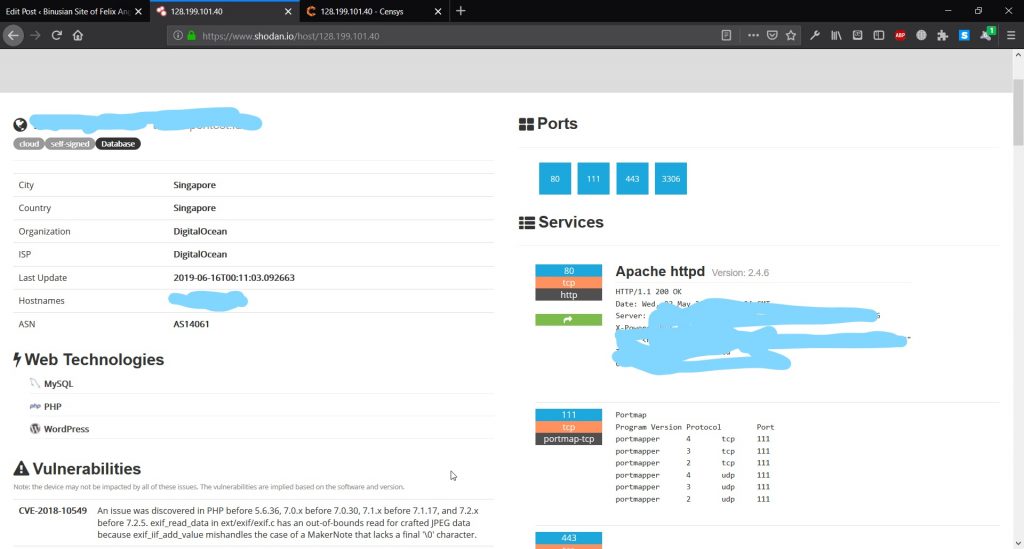
At glance, it shows similar information as Censys.io. However, if we take a closer look, it also provides us with CVE that related to the server.
It sounds like shodan is better, right? Not really. Sometimes, Shodan.io shows detail about server too detail that can cause confusion. It is better than Censys.io, but still shows similar result set as Censys.io (the Database). However, it limits the results for free users.
Both tools can search real IP. However, It can’t detect all real IP. In the end, to know for sure whether it is real IP or not, there are two step of real IP identification, which is will be discussed in the next post.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
Sometimes when you accessing certain IP, you won’t be directed to the website that you want to access. You usually be directed to a CDN server e.g. CloudFlare. It can prevent the attacker to find the real server. That’s mean the website is 100% safe, right? Not quite. While it can’t really be detected by using normal browsing, attackers can find the real IP.
There are several tools to find the real IP. We’re going to take a look at one of them, Censys.io.
Here is Censys.io:
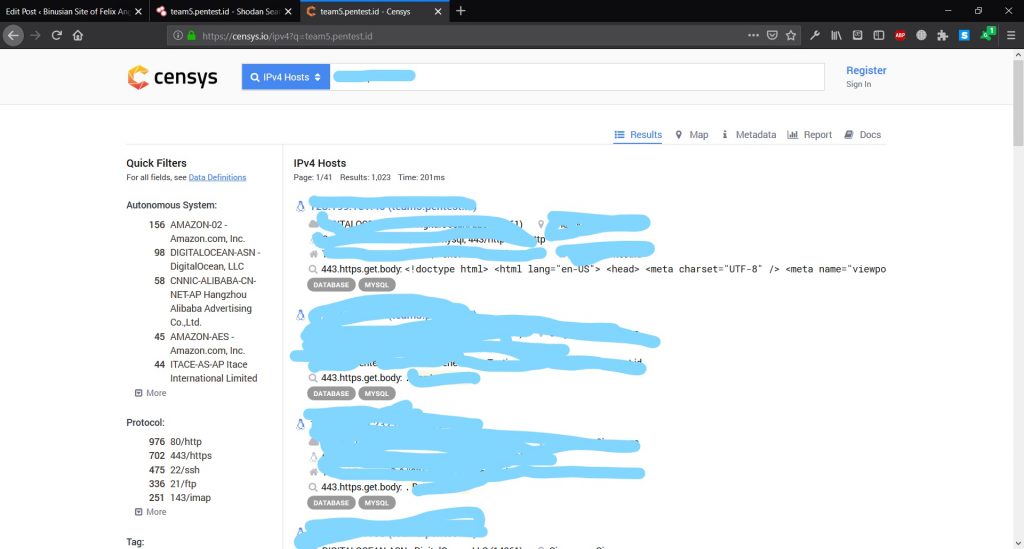
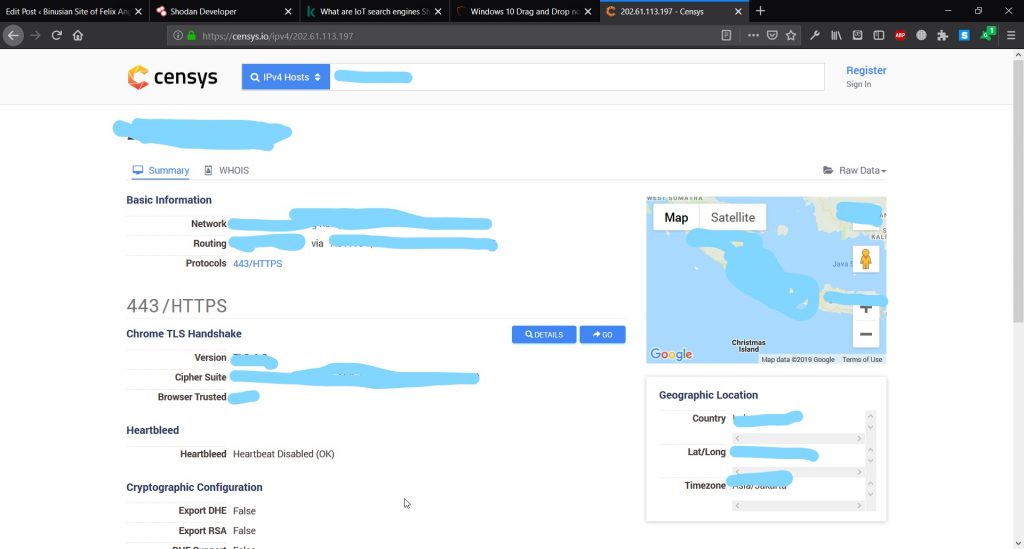
Censys.io provides the lookup for the real IP addresses. It can also show IP that correlated with the IP address.
All you have to do is just put the url into search box and go.
From the details we can know the location, routing system, etc.
However, the result details is not detail enough for the free user.
Also sometimes, it shows the unrelated and unnecessary result.
However, it doesn’t limit the search results.
That’s everything about Censys.io. In the next post, I’m going to show you about another tool for searching real IP.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
Usually, a client can’t access to the main server machine (not the website). However, if there is a hole that allows clients to use
php, client can access to the system using php injection. There are two ways to do that. One, using <pre>shell_exec()</pre> command.
Here is the example of the execution:
shell_exec(‘*nix_commands’);
This script allow us to access to the main machine.
However, we won’t be able to know what exactly happen in the server. The second one allows us to do the same, but better than the former.
The solution is to use reverse tcp. Reverse TCP is same with the former. However, it can show any progresses that regular php injection can’t offer.
In this tutorial, I’m going to use a script called php-reverse-tcp.php. You can download it from link below:
Before that, make sure that you have a machine that has a connection using static IP.
Then, download and extract the script from the website. After that, open the script using any text editor and modify these following line:
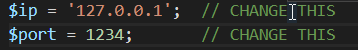
change the following line to the local IP of your machine.
you can check it using ifconfig or ipconfig
from your machine, open port that you want to use for reverse TCP by using these commands (using 4330)
>>ufw allow 4330/TCP
>>ufw enable
Then change the port number of the script to the designated port number.
Save it, then upload to the target website.
then run the following command:
![]()
After that, run the script throught web browser.
The result will be like below:

Reverse TCP may not able to do the thing that regular php injection can. However it can show more information on the display than regular php injection.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
I. Overview
The game is about fighting against pathogen using immunity mechanism.
The pathogen and immunity mechanism are represented by towers and enemies.
II. Purpose
The reason why this game is created is to educate people in general how immunity inside body fought against pathogen in simple representation.
III. Mechanism
Build towers to counter pathogen.
There is life system. Once it reached zero, it is game over, and the game will be restarted from the beginning .
Towers are upgradeable in order to to face more enemies.
Every wave increase the number of enemies.
Enemies are divided into 3:
– Bacteria (Weakness: Neutrophil)
– Parasite (Weakness: Eosinophil)
– Virus (Weakness: B-Cell)
IV. Screenshot

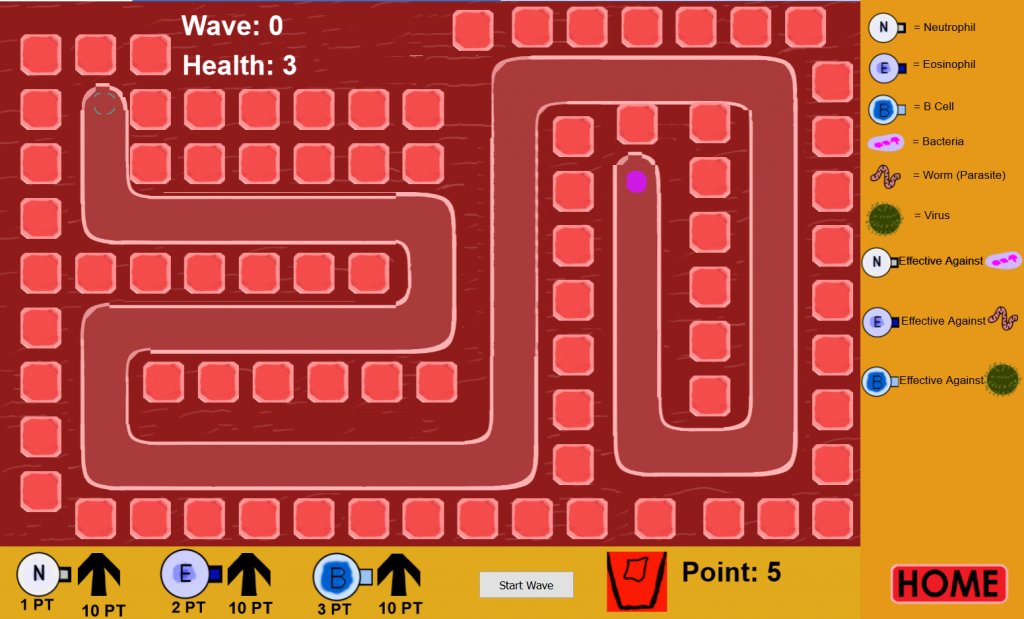
Link
Felix Anggara:
Mechanism & Artwork