WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
There are a keyword that is popular in our cyber community, Man-in-the-Middle. A man in the middle of what? What is this term?
It turns out that Man-in-the-Middle is a cyber attack that is conducted when the packet is still in the transport process, or still in the air.
The key principle of it is interception. How does it work?
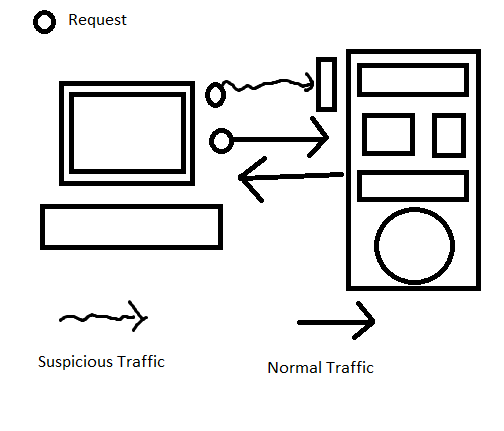
In the normal connection, the packet will be, sent straightforward to the destination.

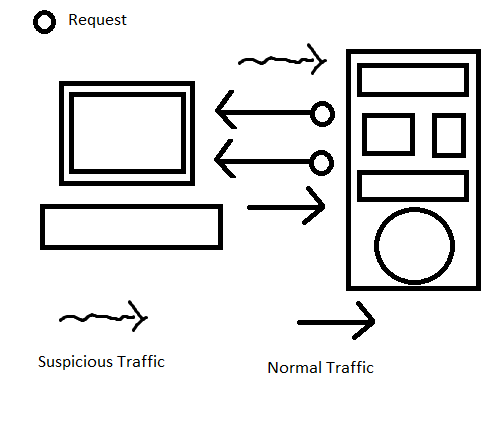
However, if the Man-in-the-Middle occurred, the things will become as below:

The packets that supposed to be sent straight to the destination are being intercepted by the third party. It will cause a serious threats for credentials, or even worse, unwanted transactions.
That is the simple explanation of Man-in-the-Middle.