WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
In one of my posts, I had demonstrated you how to use reverse TCP by pentestmonkey. But, how does reverse tcp works? In this post, we’re going to take a closer look at reverse TCP.
If the client requesting something to the server, that is forward TCP connection. Basically, the server will send a regular response as usual.
When doing something illicit, e.g. request poisoning, to the server, if the server implement proper security to handle it, the attack will be failed.
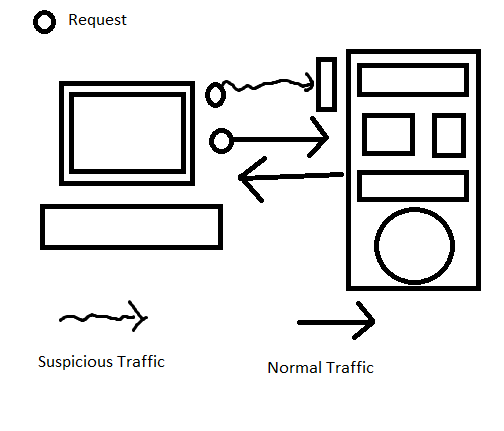
But, what happen if the, position of both is inverted? That is the thing that will cause serious security Issue.
In reverse TCP, server is the one that sent the request, and the client is the one that is responded to the request.
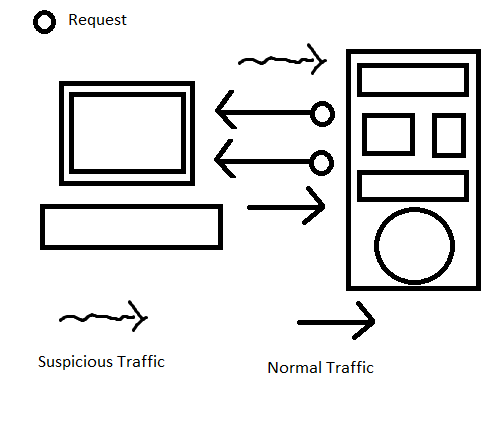
This kind of connection is dangerous, due to the firewall doesn’t block the illicit response, unlike when if the packet is a request.
That is why there are a significant number of Reverse TCP attacks.